Check Point Research (CPR) has been analysing this emerging group, which claims to heavily target the United States. Here’s what organisations need to know:
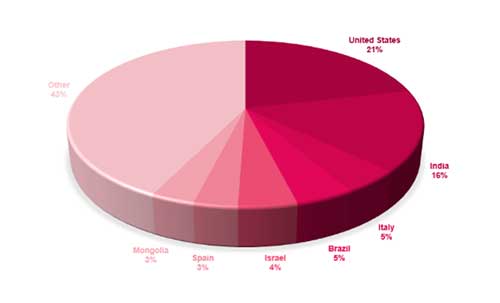
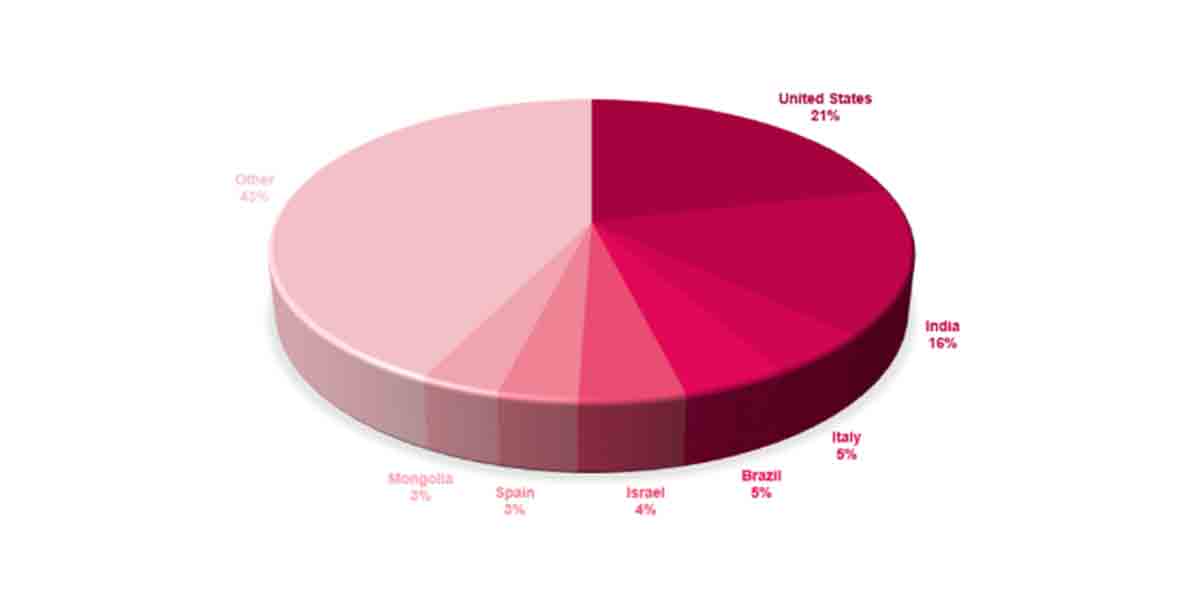
The FunkSec ransomware group first emerged publicly in late 2024, and rapidly gained prominence by publishing over 85 claimed victims—more than any other ransomware group in the month of December.
Presenting itself as a new Ransomware-as-a-Service (RaaS) operation, FunkSec favours double extortion tactics, combining data theft with encryption to pressure victims into paying ransoms.
FunkSec appears to have no known connections to previously identified ransomware gangs, and little information is currently available about its origins or operations.
CPR’s analysis indicates that the high number of published victims may mask a more modest reality, both in terms of actual victims as well as the group’s level of expertise.
Most of FunkSec’s core operations are likely conducted by inexperienced actors, with the support of AI. In addition, it is difficult to verify the authenticity of the leaked information as the group’s primary goal appears to be to gain visibility and recognition.
Evidence suggests that in some instances, the leaked information was recycled from previous hacktivist-related leaks, raising questions about its authenticity.
Additionally, FunkSec has ties to hacktivist activity, with members operating in Algeria. This highlights the increasingly blurred line between hacktivism and cybercrime, emphasising the challenges in distinguishing one from the other.
Whether such a distinction genuinely exists—or whether the operators are even aware of or concerned with defining it—remains uncertain.
More importantly, it also calls into question the reliability of current methods for assessing the risk posed by ransomware groups, especially when those assessments rely on the public claims of the actors themselves.
Closer analysis of FunkSec’s activities and DarkWeb discussions offers some tantalising hints about the group, namely that their motivations seem to straddle the line between hacktivism and cybercrime.
Interestingly, some members linked to FunkSec previously engaged in hacktivist activities, adding a complex layer to their operations and raising questions about their true objectives. This blend of tactics and backgrounds made FunkSec a particularly intriguing case for deeper investigation.
For the full CPR report on FunkSec, visit here.